Security
SentiOne Automate was designed with On-Premise and Cloud deployments within Customer's infrastructure in mind. Logical structure of the applications is built upon microservices paradigm, our applications are mostly stateless and the data is separated from the application's logic. This way we can deliver updates without the need of having direct access to the data. What's more logs of our applications are fully anonymized, which allows sharing them for diagnosis without worrying about privacy of Customer's clients. All communication between applications in Kubernetes cluster and databases and users is secured (data encryption in transit).
Our current reference deployment relies on running our components in safe internal network, with the only external access allowed through the API of Gateway service. Our components communicate by using HTTP protocol and exchanged data is in JSON format.
It's possible to extend security of our solution with following functionalities:
- Extended password policy (password minimum length 12 characters)
- Integration with external authentication services like Kerberos. See SSO Server
- Limiting access to specific ports to dedicated IP address pool (firewall) - depending on channels supported all incoming traffic should be blocked and limited to whitelisted IPs
- Communication tunneling with use of VPN
- Use of user's certificates while communicating with HTTPS protocol
- Use of advanced authentication and authorization methods provided with DB vendors
- Encrypt hard drives to provide encryption at rest
- Enforce 2FA within Organization
Session management
Additional configuration may be applied to improve security
Maximum session age
play.http.session.maxAge: 12h # hoursAfter 12 hours (default) after login session cookie will expire and user will be logged out.
Session expiration time
chatbots.admin.session-expiration-time: 30m # minutes Inactivity for 30 minutes (default) will log out user, however any interaction will extend session.
Session id logging
chatbots.admin.is-session-id-logging-enabled: true When enabled logs will not only include "USER:xxx, IP:xxx" but also "SESSION_ID:xxx"
Limiting login requests
You can configure the platform to limit login request in 1-hour sliding window per IP
chatbots.admin {
(..)
login-tries-per-hour: 10
}env:
(...)
web:
(...)
loginAttempts:
maxPerHour: 10When the failed login limit is reached for IP any further log in attempt will fail.
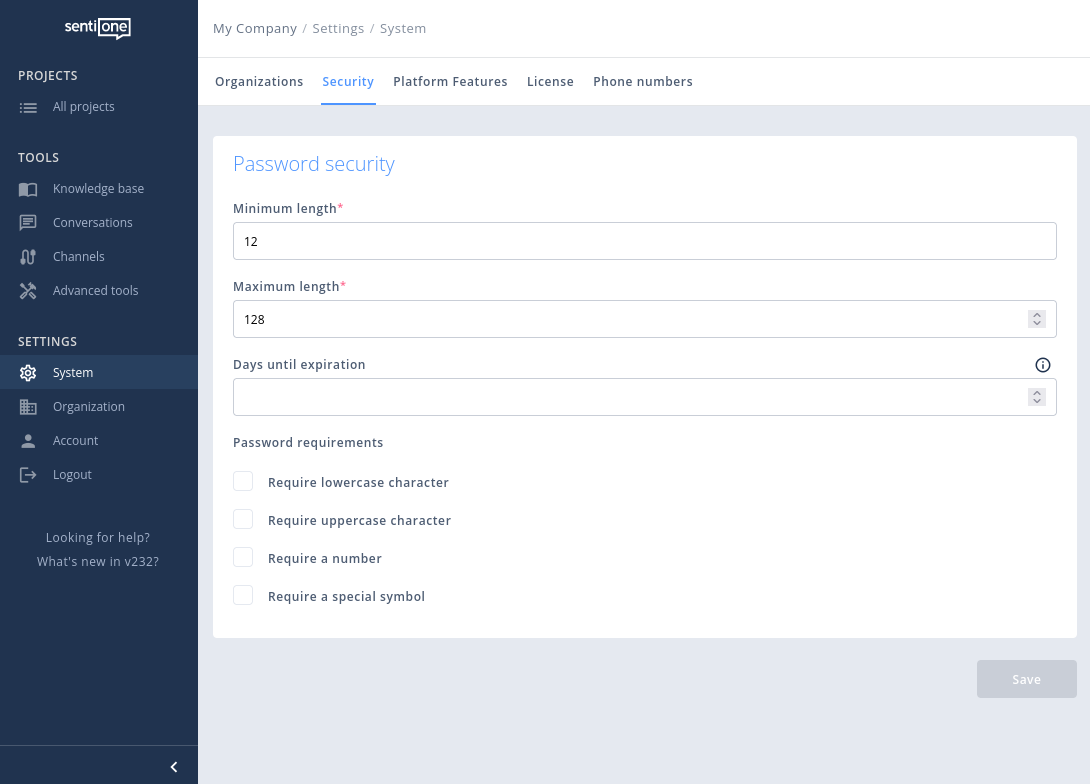
Password policy
System admins can configure the password policy globally, as in the example below.
Updated 4 months ago
